
Hackers are conducting widespread exploitation of a critical WooCommerce Payments plugin to gain the privileges of any users, including administrators, on vulnerable WordPress installation.
WooCommerce Payments is a very popular WordPress plugin allowing websites to accept credit and debit cards as payment in WooCommerce stores. According to WordPress, the plugin is used on over 600,000 active installations.
On March 23rd, 2023, the developers released version 5.6.2 to fix the critical 9.8-rated vulnerability tracked as CVE-2023-28121. The flaw affects WooCommerce Payment plugin versions 4.8.0 and higher, with it being fixed in versions 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2, 5.6.2, and later.
As the vulnerability allows any remote user to impersonate an administrator and take complete control over a WordPress site, Automattic force installed the security fix of WordPress installations utilizing the plugin.
At the time, WooCommerce said there was no known active exploitation of the vulnerability, but researchers warned that due to the critical nature of the bug, we would likely see exploitation in the future.
Flaw actively exploited
This month, researchers at RCE Security analyzed the bug and released a technical blog on the CVE-2023-28121 vulnerability and how it can be exploited.
The researchers explain that attackers can simply add an ‘X-WCPAY-PLATFORM-CHECKOUT-USER’ request header and set it to the user ID of the account they wish to impersonate.
When WooCommerce Payments sees this header, it will treat the request as if it was from the specified user ID, including all of the user’s privileges.
As part of the blog post, RCE Security released a proof-of-concept exploit that uses this flaw to create a new admin user on vulnerable WordPress sites, making it easy for threat actors to take complete control over the site.
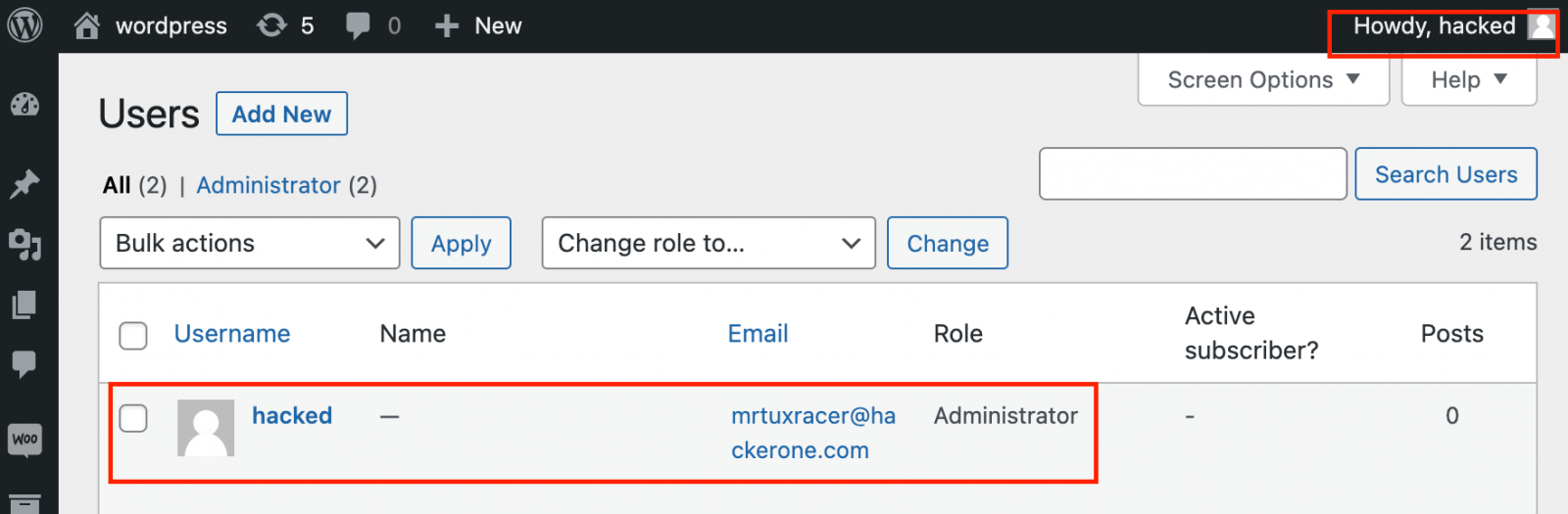
Using the exploit to create the ‘hacked’ administrator account
Using the exploit to create the ‘hacked’ administrator account
Source: RCE Security
Today, WordPress security firm Wordfence warned that threat actors are exploiting this vulnerability in a massive campaign targeting over 157,000 sites by Saturday.
“Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023,” explains Wordfence.



I visited multiple blogs however the audio feature for audio songs current at this web site is actually marvelous.
my web page :: how to get more followers
on instagram (wwd.com)
Hi Dear, are you truly visiting this web site regularly, if so then you will absolutely get fastidious experience.
Also visit my web site: Bonanza Navidad (Carmelo)
whoah this weblog is fantastic i love reading your posts.
Keep up the great work! You already know, a lot of people are looking around
for this information, you can aid them greatly.
Look into my web blog :: Slot Bonanza pragmático
Undeniably believe that which you stated. Your favorite justification seemed to be on the
net the easiest thing to be aware of. I say to you, I
definitely get irked while people think about worries that they
just do not know about. You managed to hit the nail upon the top as well
as defined out the whole thing without having side effect , people can take a signal.
Will likely be back to get more. Thanks
My blog … Tragamonedas Dulce Bonanza (http://www.ad-links.org)
Just want to say your article is as astounding.
The clarity on your post is simply great and i could suppose you are a professional on this subject.
Well along with your permission let me to seize your RSS feed to stay up to date with
impending post. Thank you a million and please carry on the
gratifying work.
Take a look at my site; betano sweet bonanza
I know this if off topic but I’m looking into starting my own blog and was wondering
what all is required to get set up? I’m assuming
having a blog like yours would cost a pretty penny? I’m not
very web smart so I’m not 100% positive. Any
suggestions or advice would be greatly appreciated.
Thank you
Here is my blog post :: best gold ira companies
Appreciate the recommendation. Let me try it out.
Here is my blog post: Bonanza pragmático – Marian
–
No matter if some one searches for his vital thing,
therefore he/she wishes to be available that in detail, thus that thing is maintained over here.
Stop by my web-site :: Revisão do slot Sweet Bonanza
I have been exploring for a little for any high quality articles or weblog posts in this sort of
area . Exploring in Yahoo I eventually stumbled upon this website.
Reading this info So i’m happy to exhibit that I’ve an incredibly excellent uncanny feeling I came upon just what I needed.
I most no doubt will make sure to do not omit this web site and provides it a glance regularly.
Feel free to visit my web-site Juego Dulce Bonanza (910bs4kt7dv9g.com)
Hi! Would you mind if I share your blog with my zynga group?
There’s a lot of folks that I think would really enjoy your content.
Please let me know. Thank you
Also visit my blog post … Ejemplos de grandes ganancias en Dulce Bonanza
cialis experience reddit
cialis greece
brand cialis
oxycodone 30 mg pharmacy
mexican pharmacy klonopin
buy viagra without a script
viagra 40 mg
cialis daily price
buying cialis without a prescription
sildenafil 100 mg generic price
tour de pharmacy watch online
price of cialis at walmart
how to use cialis
cialis 5mg best price
what is tadalafil
buy sildenafil mexico
cheap viagra australia fast delivery
cialis online canada
where do you inject liquid cialis
Great information. Lucky me I found your site by chance (stumbleupon).
I’ve saved it for later!
My page: generic cialis tadalafil
cheap cialis 5mg
tadalafil (в„ћ) 20mg tablet
metronidazole harmful
mechanism of action of folate antagonists sulfamethoxazole
VZfRekUduhKyGqr
whoah this weblog is wonderful i like studying your posts.
Keep up the great work! You know, lots of people are
hunting around for this info, you can aid them greatly.
Also visit my site – can you drink and take shrooms