Hackers are conducting widespread exploitation of a critical WooCommerce Payments plugin to gain the privileges of any users, including administrators, on vulnerable WordPress installation.
WooCommerce Payments is a very popular WordPress plugin allowing websites to accept credit and debit cards as payment in WooCommerce stores. According to WordPress, the plugin is used on over 600,000 active installations.
On March 23rd, 2023, the developers released version 5.6.2 to fix the critical 9.8-rated vulnerability tracked as CVE-2023-28121. The flaw affects WooCommerce Payment plugin versions 4.8.0 and higher, with it being fixed in versions 4.8.2, 4.9.1, 5.0.4, 5.1.3, 5.2.2, 5.3.1, 5.4.1, 5.5.2, 5.6.2, and later.
As the vulnerability allows any remote user to impersonate an administrator and take complete control over a WordPress site, Automattic force installed the security fix of WordPress installations utilizing the plugin.
At the time, WooCommerce said there was no known active exploitation of the vulnerability, but researchers warned that due to the critical nature of the bug, we would likely see exploitation in the future.
Flaw actively exploited
This month, researchers at RCE Security analyzed the bug and released a technical blog on the CVE-2023-28121 vulnerability and how it can be exploited.
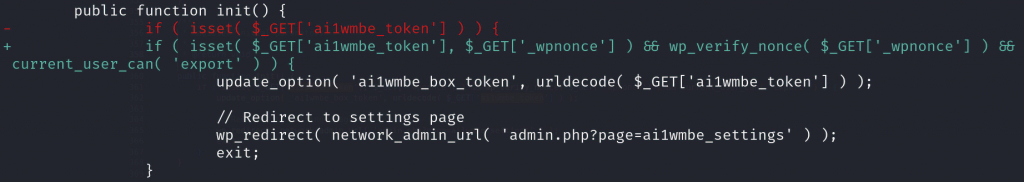
The researchers explain that attackers can simply add an ‘X-WCPAY-PLATFORM-CHECKOUT-USER’ request header and set it to the user ID of the account they wish to impersonate.
When WooCommerce Payments sees this header, it will treat the request as if it was from the specified user ID, including all of the user’s privileges.
As part of the blog post, RCE Security released a proof-of-concept exploit that uses this flaw to create a new admin user on vulnerable WordPress sites, making it easy for threat actors to take complete control over the site.
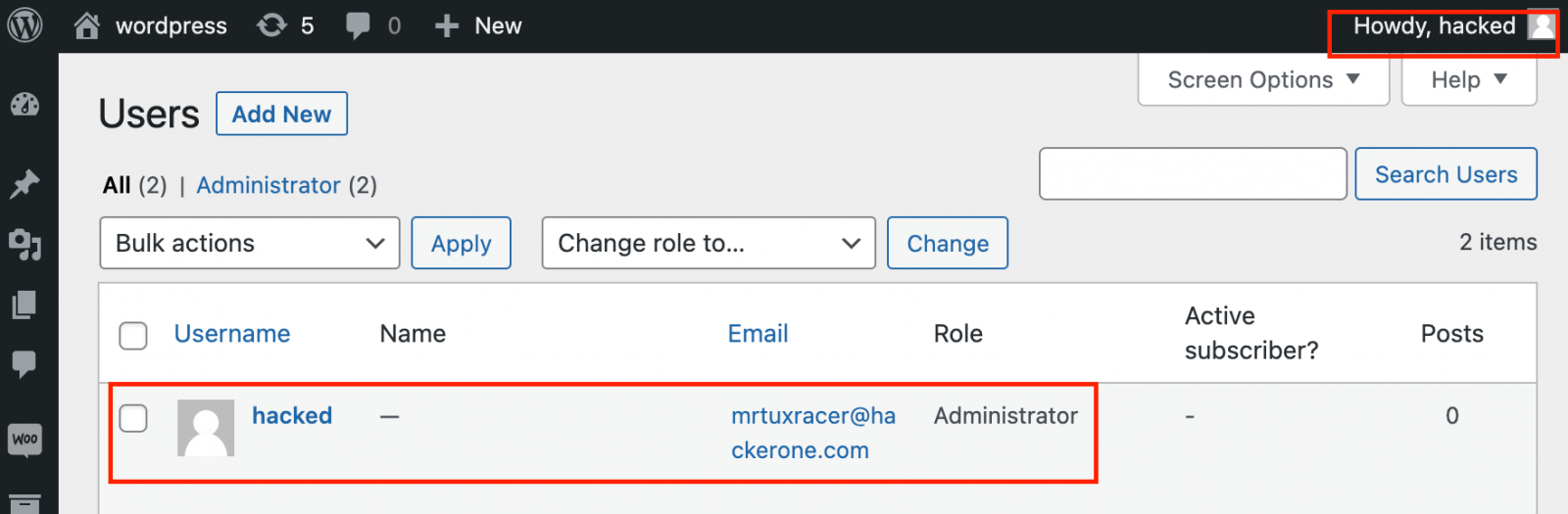
Using the exploit to create the ‘hacked’ administrator account
Using the exploit to create the ‘hacked’ administrator account
Source: RCE Security
Today, WordPress security firm Wordfence warned that threat actors are exploiting this vulnerability in a massive campaign targeting over 157,000 sites by Saturday.
“Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023,” explains Wordfence.